Cybersecurity audit company
Cybersecurity audit company
A computer security audit is a comprehensive evaluation of a company’s information technology infrastructure. This evaluation may include testing of software, hardware, security policies, and procedures.
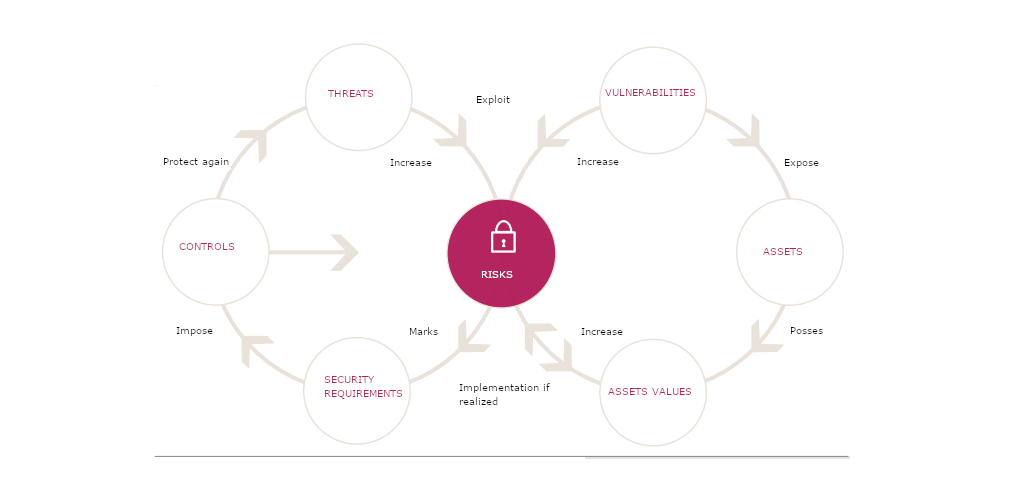
The primary objective of a computer security audit is to detect vulnerabilities and threats that could jeopardize the confidentiality, integrity, and availability of the company’s information.
The IT audit allows us to have a clear view of the security status of our infrastructure and helps identify weak points that need improvement. In this way, preventive measures can be taken to protect the company’s data and reduce the risks of cyberattacks.
audit points
Types of audits
nternal security audit
The main objective of a security audit is to detect possible weaknesses and risks in the structure of a company or organization’s system. During the process, possible access routes that could be used by an internal attacker are identified, and the probability of suffering an attack and its possible consequences are calculated.
In particular, the security audit focuses on analyzing possible attacks that could lead to theft of company information and provides solutions to minimize the chances of an internal attack.
Performing security audits regularly allows companies to maintain greater control over the security of their systems, thereby improving their integrity, confidentiality, and availability.


External security audit
The purpose of an external security audit is to evaluate a company’s security level on the Internet, identifying possible weaknesses and vulnerabilities that could be exploited by an external attacker. Through different techniques and tools, tests are performed to obtain sensitive information without prior knowledge of the victim.
Conducting an external security audit enables knowledge of the technical vulnerabilities of systems external to the company, as well as the possible consequences that could result from an attack.
Web audit
To improve the security of websites and web applications, an audit examines various critical aspects such as protection against possible threats, underlying infrastructure, and possible vulnerabilities based on the development language and deficiencies in application logic.
The main objective of this audit is to detect any implementation failures that could compromise the security of the application or website.


nfrastructure audit
An infrastructure audit is an evaluation process that seeks to identify possible weaknesses and vulnerabilities in the technological infrastructure of an organization.
It is important to note that the infrastructure audit can include both the review of the perimeter network and internal networks, as both can present security risks to the organization.
Penetration testing
This type of testing is used to evaluate the security of an organization’s systems and networks by simulating real attacks and using ethical hacking techniques.
The goal is to detect possible vulnerabilities and weak points in the infrastructure and provide solutions to improve security and reduce the risks of a real attack.

REASONS TO CONDUCT A CYBERSECURITY AUDIT
BENEFITS OF A CYBERSECURITY AUDIT
PREVENTS ATTACKS CREATES PROTOCOLS EFFICIENCY OF SYSTEMS AND PROGRAMS IMPROVES DATA SECURITY AND PROTECTION NETWORK AND EQUIPMENT PROTECTION SYSTEMS
Cybersecurity audits are essential for assessing security performance and providing recommendations to strengthen an organization’s security posture. During the audit, assets are analyzed and major security vulnerabilities and threats are identified. Guidance is then provided on necessary measures to improve the level of security.
Currently, having strong security policies is essential, especially regarding secure passwords, security in remote work, and devices that handle sensitive information.
At DDROM, we know how we can help you protect your company.